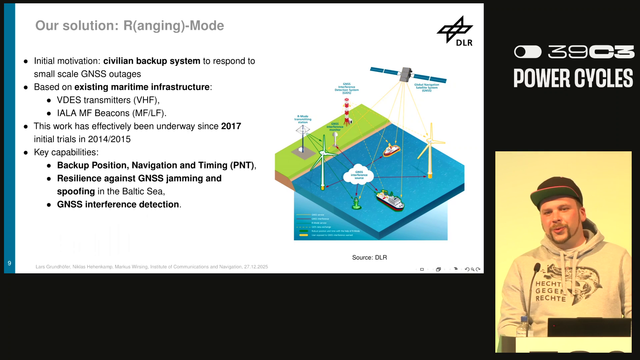
The proposed solution to provide a workaround uses existing maritime systems like VDES transmitters and IALA MF Beacons. The aim to provide backup time, navigation and positioning data. This solution is aimed at detecting GNSS jamming and spoofing. #39c3
The team has been doing testing with Germany, Poland, Denmark, Poland, Norway, Sweden and Finland using a testbed where a jammer showed up. #39c3
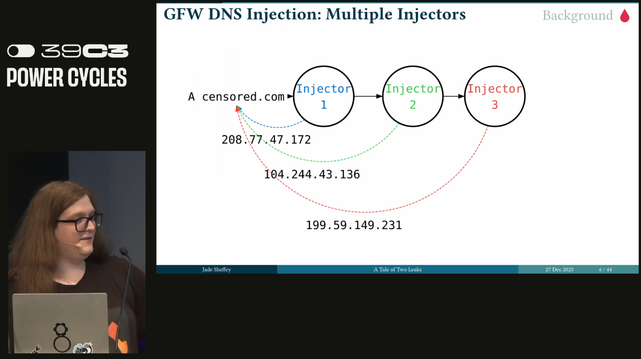
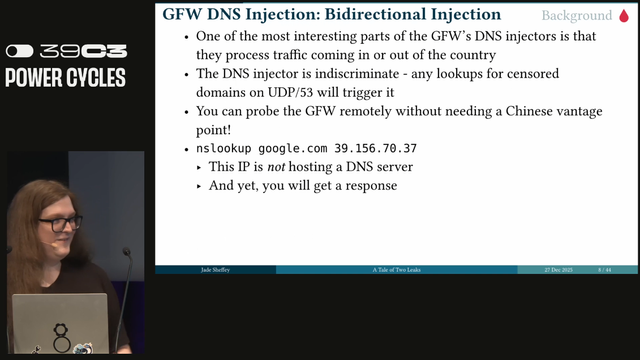
The censorship system uses TCP resets but also relies on DNS injection which will respond with bogus IP addresses. You can send DNS requests to the great firewall outside of China to see how the system responds. #39c3
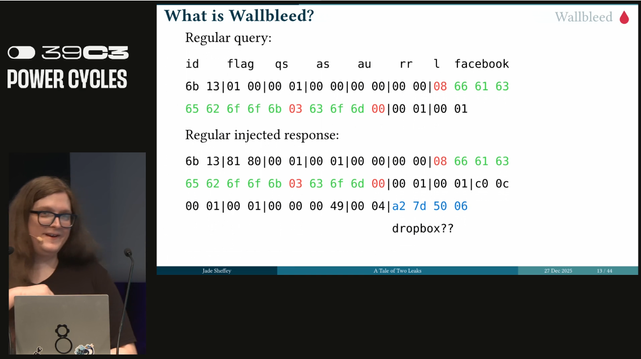
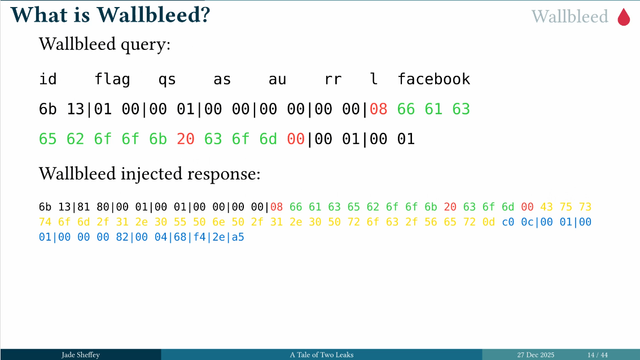
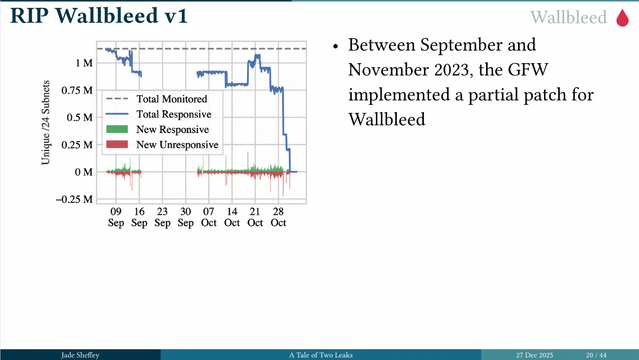
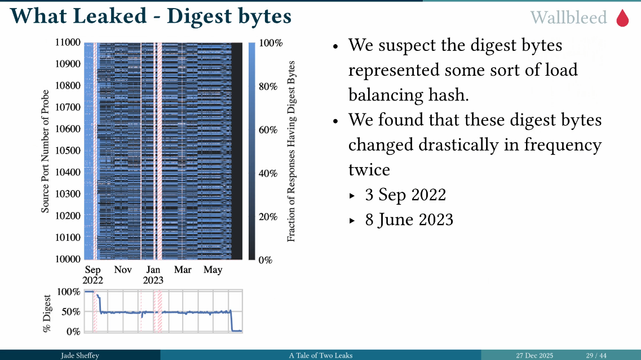
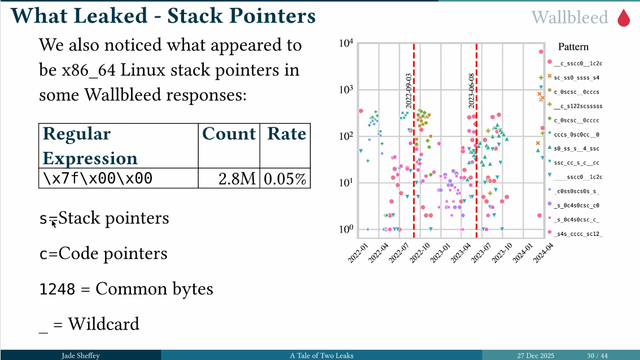
The researches found that the responses were dumping memory. This wallbleed query could return 124 bytes of memory. This vulnerability was patched in 2023. #39c3
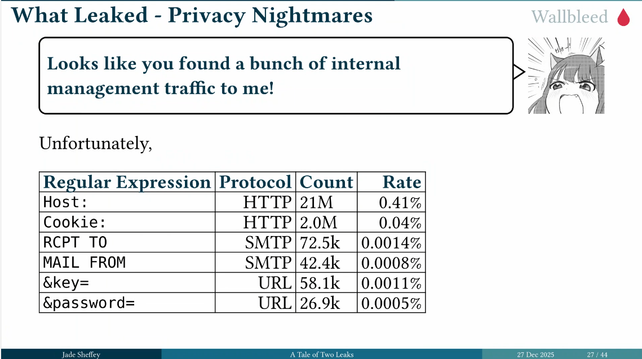
By using wallbleed, the researchers were able to find what people were browsing. Some interesting patterns emerged and also allowed to them to see what changes were being made on the great firewall. #39c3
A Tale of Two Leaks: How Hackers Breached the Great Firewall of China by Jade Sheffey #39c3
🧵
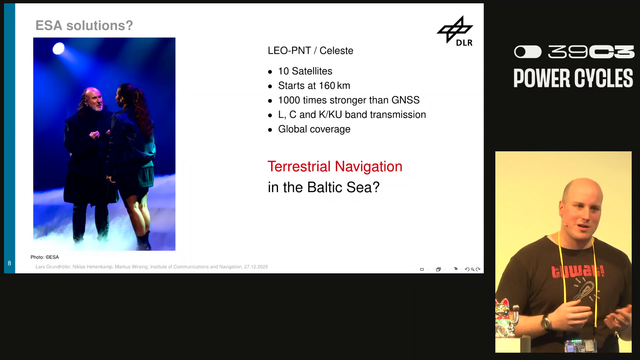
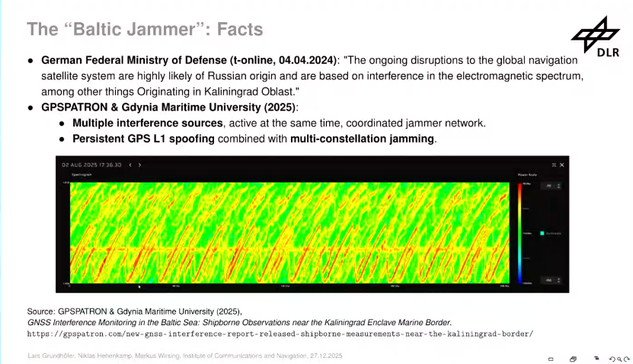
Who cares about the Baltic Jammer? – Terrestrial Navigation in the Baltic Sea Region by Lars, Niklas and Markus #39c3 🧵
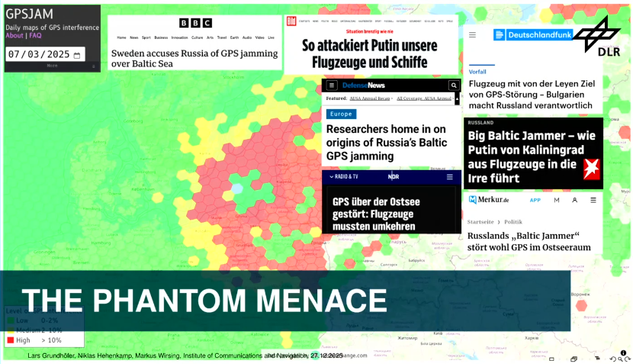
GPS Jamming is a common issue around eastern Europe and presents a significant issue as airplanes and ships depending on this for navigation. #39c3
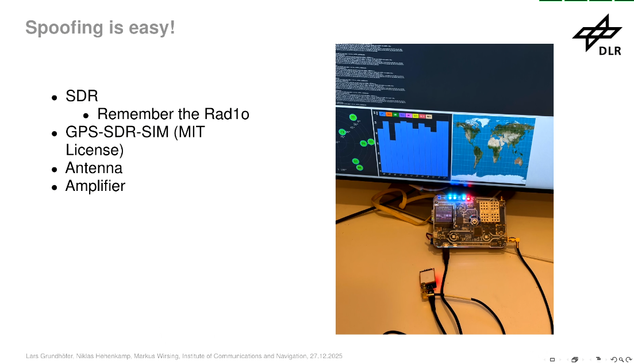
Jamming these signals are quite easy using commonly available SDR devices. Research has shown that it is not only jamming that is happening but also GPS spoofing as well. The jamming and spoofing is happening from different devices and different origins and the interference is coming from Russia. #39c3
To sign or not to sign: Practical vulnerabilities in GPG & friends by 49016 & Liam #39c3 🧵