That was a really good talk by @pluralistic. Very interesting idea that we get rid of anticircumvention laws as a way to fight back against the large tech companies. For me it is still problematic that pentesters can be held liable for finding vulnerabilities, disclosing these vulnerabilities or trying to fix these vulnerabilities. #39c3
A post-American, enshittification-resistant internet by Cory Doctorow
States are reluctant to create safeguards around these technologies, to keep an edge on the battlefield for intelligence.
When we have seen in previous years that zero days can be weaponized to affect a large number of people and companies like we saw when eternal blue was weaponized in the WannaCry and NotPetya campaigns which affected a large number of companies and caused major financial loses. Should these vulnerability markets be allowed?
Something to consider is that hacking tools go beyond surveillance, they can hamper data integrity by adding, removing or modifying data which means that it could tamper with evidence.
The use of surveillance in this way poses real dangers to democracy especially when law enforcement and intelligence agencies are going way beyond what is legally allowed. #39c3
Investigative journalists investigating corruption as well as lawyers are frequently targeted.
In Poland, one of the targets were infected by Peagsus and 10 years of text messages were extracted and then re-arranged by law enforcement and presented on TV. When the judge was asked about this, they had no idea around what they were allowing.
Once a person is investigated or targeted, they do not get notified which is contravening the states requirements under the EU to notify targets of secret surveillance. #39c3
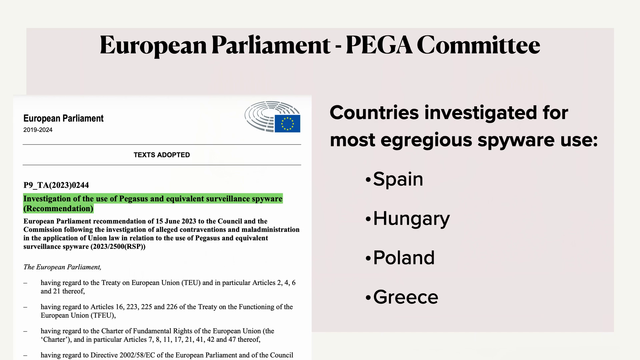
Countries including Spain, Hungary, Poland and Greece have been investigated for using spyware. A Pega coalition has been established to litigate the use of spyware by law enforcement and intelligence agencies. #39c3
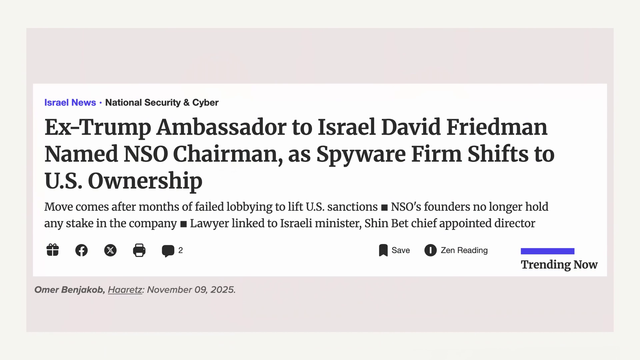
These companies are not just passive partners or resellers, they are actively involved in sale and use of the software. The use of this software is disproportionate and does not have judicial oversight. While the founders of NSO Group have left the company, they are still involved in the wider industry. #39c3
The Catalan Gate report showed how members of the European Parliament, civil society members and lawyers representing prominent Catalans were infected by Peagsus which is built by the NSO Group. Peagsus was used without any judicial authorization or oversight which is illegal. Charges were filed against them for this behavior. Peagsus was installed using zero days that don't require user interaction. The NSO group has a group of legal entities that they use to sell their software. The entities in Luxemborg shared the same board of directors and the speakers wanted to demonstrate corporate culpability. This investigation was the first in the world to look at NSO group directors involved with spyware in Europe. #39c3
In 2017, Catalonia voted in a referendum for the independence of Catalonia or the right to self determination. In May 2020, one of the lawyers involved in the defense of politicians were infected by Peagsus which was reported on by Citizen Lab. #39c3