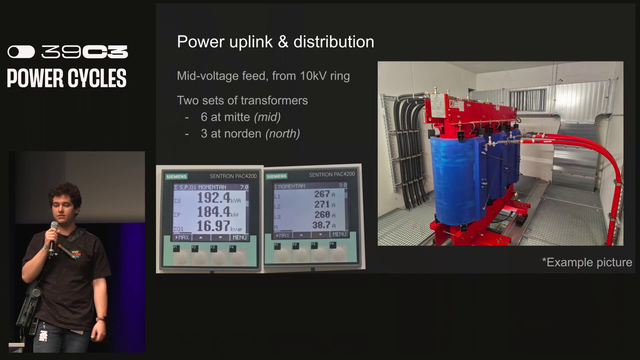
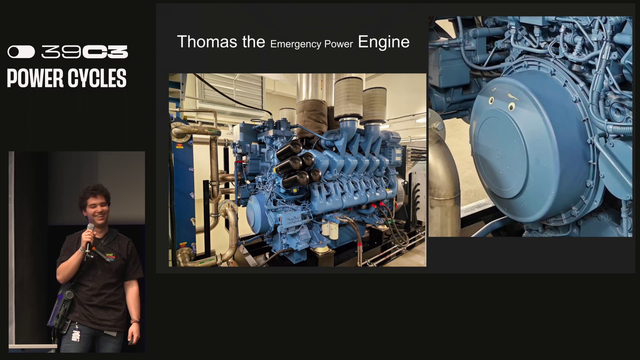
Congress is powered by a 10kV ring through 2 transformers. There is an emergency "thomas the tank engine" generator for emergency power. #39c3
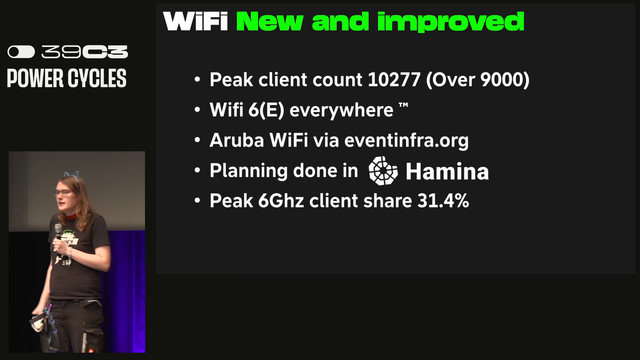
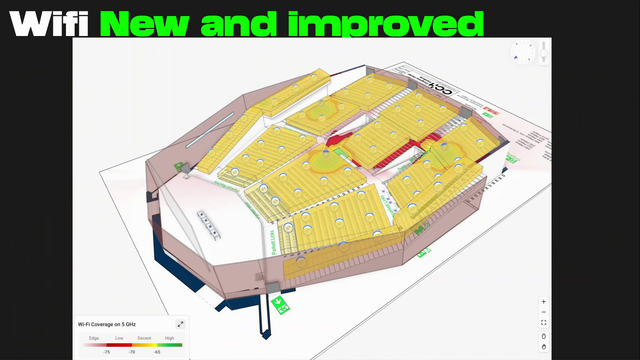
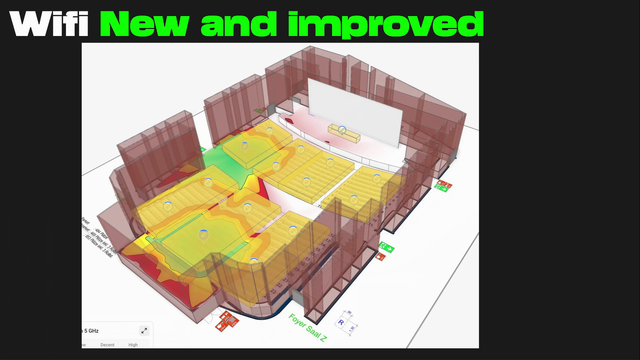
The team managed to deploy WiFi 6 across the bulding with a peak of 10277 clients. Planning was done in Hamina which made the wifi deployment better. Almost a third of capacity was over 6Ghz. #39c3
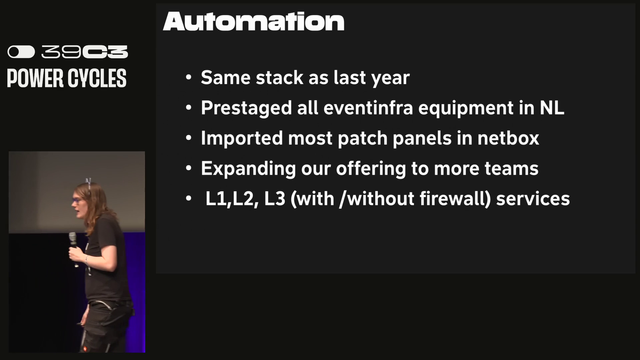
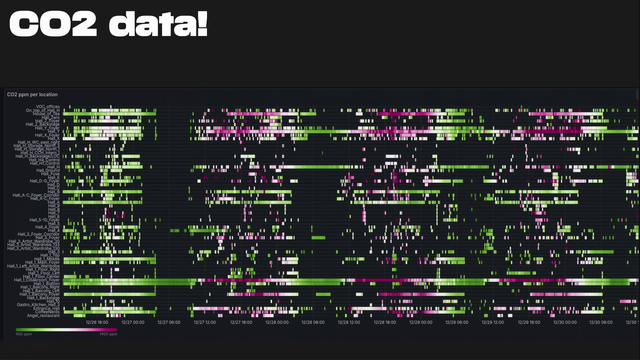
The team used the same automation stack as last year. A lot of equipment was prestaged which made deployment faster. All of the patch panels were imported into netbox. DoT on the resolvers and C02 monitoring was done by BLE beacons. #39c3
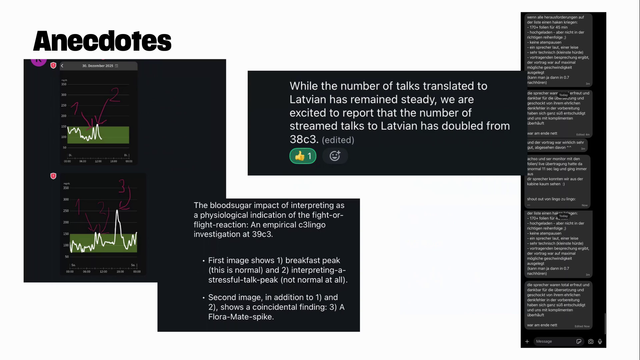
One speaker had 170 slides for a 45 minute talk and had practiced to get a high word per minute rate which made this very difficult to translate. Doing this takes a significant toll on the translation team. #39c3
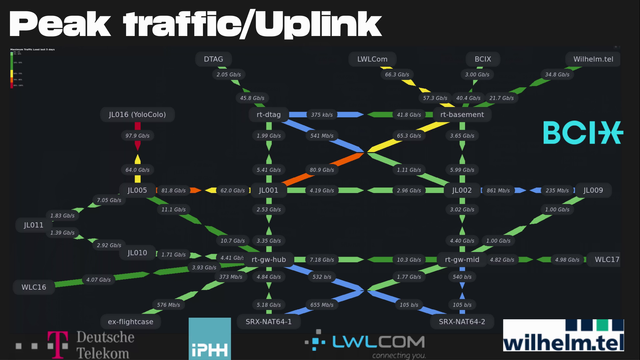
Weather map of the traffic following through congress. The YoloColo saturated the 100 Gbps link. 300 Gbit of capacity was provided by several partners. #39c3
A Tale of Two Leaks: How Hackers Breached the Great Firewall of China by Jade Sheffey #39c3
🧵
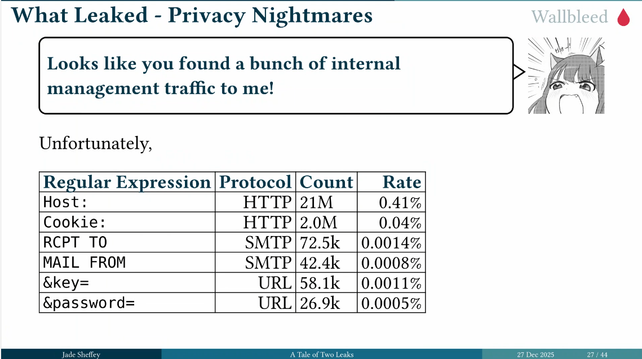
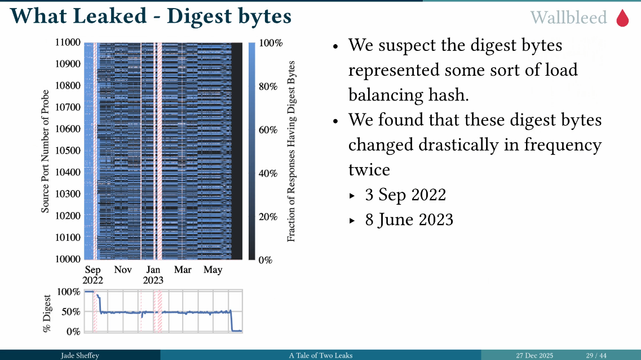
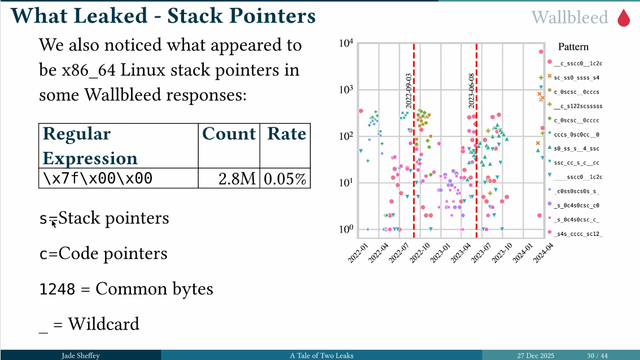
By using wallbleed, the researchers were able to find what people were browsing. Some interesting patterns emerged and also allowed to them to see what changes were being made on the great firewall. #39c3
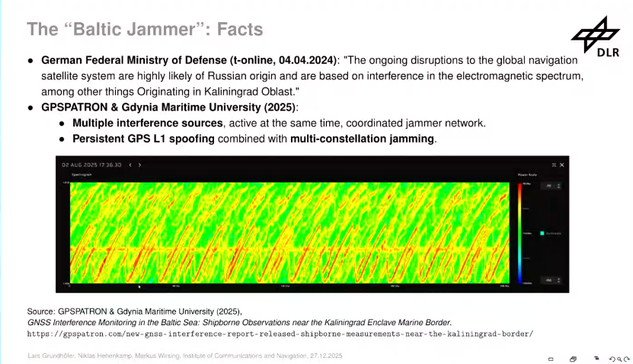
The team has been doing testing with Germany, Poland, Denmark, Poland, Norway, Sweden and Finland using a testbed where a jammer showed up. #39c3
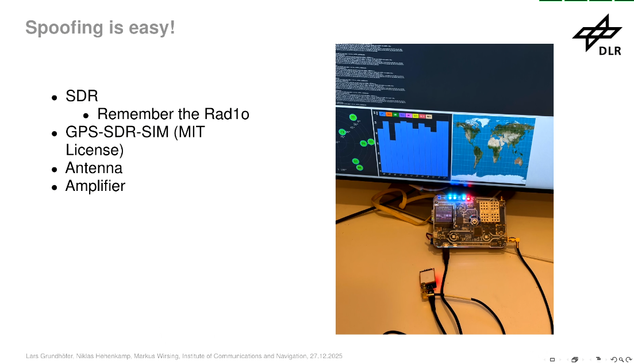
Jamming these signals are quite easy using commonly available SDR devices. Research has shown that it is not only jamming that is happening but also GPS spoofing as well. The jamming and spoofing is happening from different devices and different origins and the interference is coming from Russia. #39c3